Configuring BitLocker using Microsoft Intune & store keys in Microsoft 365
- aymeneljaziri
- 3 juil. 2025
- 6 min de lecture
BitLocker is a disk encryption feature that protects data stored on Windows 10/11 devices against theft or loss, so that it can only be accessed by authorized persons. BitLocker uses a secure platform module (TPM) to store encryption keys and protect them against attack. BitLocker can also use other protection methods, such as a password, USB key or PIN.
Microsoft Intune is a device and application management service that enables organizations to control and secure corporate data on mobile devices and computers. Microsoft Intune and BitLocker can work together to ensure optimal data and device protection. For example, Intune can configure and manage BitLocker settings, save recovery keys in Azure AD, and apply compliance policies based on encryption status .
In this article, I'll show you how to enable and configure BitLocker using Intune and export the BitLocker key to Microsoft Azure. We will use Microsoft Intune to configure BitLocker drive encryption on devices running Windows 10 or 11. The manual explains how to deploy BitLocker using Intune for Windows devices.

I - BitLocker Intune prerequisites
BitLocker for Intune is available on devices running Windows 10/11. Enabling BitLocker using Intune requires the following prerequisites to be in place:
You will need a valid Microsoft Endpoint Manager (Intune) license.
Devices must be connected to Azure AD or Hybrid Azure AD.
Devices must not be encrypted with third-party disk encryption tools such as McAfee Disk Encryption. If devices are already encrypted with other solutions, you will first need to decrypt them completely before deploying BitLocker using Intune.
End devices must be equipped with a TPM chip version 1.2 or higher (TPM 2.0 strongly recommended).
BIOS must be set to UEFI.
To manage BitLocker in Intune, your account must have the applicable role-based access control (RBAC) permissions.
II - BitLocker configuration and deployment methods with Intune
Intune lets you configure and deploy BitLocker policy using two methods:
Create a device configuration profile for BitLocker and deploy it to devices.
Create an endpoint security policy for BitLocker, configure it and deploy it to devices.
You can use any of the above procedures to create the type of policy you prefer. The recommended approach is to create an endpoint security policy and configure BitLocker using Intune for Windows devices.
III - Settings required to silently enable BitLocker using Intune
Depending on the type of policy you're using, you can silently enable BitLocker using Intune:
1 - Endpoint security disk encryption policy
Configure the following settings in the BitLocker profile
Hide prompt about third-party encryption = Yes.
Allow standard users to enable encryption during Autopilot = Yes.
Require Key File Creation = Blocked or Allowed.
2 - BitLocker Device configuration policy
Configure the following settings in the endpoint protection template or in a custom settings profile
Warning for other disk encryption = Block.
Allow standard users to enable encryption during Azure AD Join = Allow.
IV - Enabling and configuring Bitlocker with Intune
We'll now look at how to use Intune to activate, configure and deploy BitLocker. This will enable BitLocker drive encryption to be configured on devices running Windows 10/11.
The high-level steps for enabling and configuring BitLocker using Intune are as follows:
Enable BitLocker with Intune
Create a configuration profile for BitLocker in Intune
Configure BitLocker policy with Intune
Monitor BitLocker encryption status
V - Create a BitLocker policy in Intune
In this step, we'll create a new security policy for BitLocker in Intune by following these steps:
Log into the Microsoft Endpoint Manager administration center (Intune Admin Center).
Select Endpoint security > Disk encryption > Create Policy.
Set the following options:
Platform : Windows 10/11
Profile : BitLocker

Enter a name for your Policy :
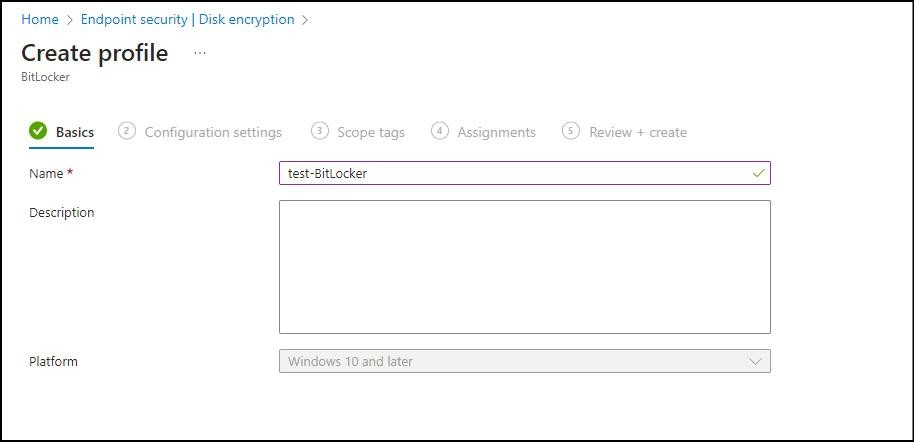
in the second "Configuration Settings" window is divided into two sections:
1 - BitLocker section
Require Device Encryption
Enabled
Allows the administrator to require encryption to be enabled using BitLocker device encryption.
Allow Warning For Other Disk Encryption
Disabled
Allows the administrator to disable all user interfaces (notification for encryption and warning prompt for encryption of other disks) and silently enable encryption on user machines.
Allow Standard User Encryption
Enabled
Enables the administrator to apply the "RequireDeviceEncryption" policy in scenarios where the policy is applied when the logged-in user is not an administrator or standard user.
Configure Recovery Password Rotation
Refresh on for Azure AD-joined devices
Allows the administrator to configure digital recovery password rotation when using the operating system and fixed drives on devices connected to the AAD and Hybrid domains.

2 - Administrative templates section
In this section, we'll apply the following settings:
Select disk encryption method and encryption strength (Windows 10 [Version 1511] and later): Enabled
Select encryption method for removable data drives : AES-CBC 128-bit (default)
Select encryption method for operating system drives : XTS-AES 128-bit (default)
Select encryption method for fixed data drives : XTS-AES 128 bits (default)

In this section, we'll apply the following settings:
Enforce drive encryption type on operating system drives : Enabled
This policy parameter lets you configure the type of encryption used by BitLocker Drive Encryption. This setting is applied when BitLocker is enabled.
Select the encryption type: (Device) : Full encryption
choose "Full encryption" instead of "Used Space".
Require additional authentication at startup : Enabled
This policy setting allows you to configure whether BitLocker requires additional authentication at each computer startup, and whether you use BitLocker with or without Trusted Platform Module (TPM). If you wish to use BitLocker on a computer without TPM, check the box "Allow BitLocker without compatible TPM".
Configure TPM startup key and PIN : Allow startup key and PIN with TPM
Allow BitLocker without a compatible TPM (requires a password or a startup key on a USB flash drive) : False
Configure TPM startup : Allow TPM
Configure TPM startup PIN : Allow startup PIN with TPM
Configure TPM startup key : Allow startup key with TPM

The next step is to create a Tag , I leave it as default

The next step is to assign a group of machines on which to apply encryption. In my case, I've chosen all devices.
You can add exclusions in the "Excluded Groups" section below.

The last step is to validate and create the encryption rule:

VI - Monitoring BitLocker from Intune
After deploying BitLocker using Intune, the next step is to monitor the status of BitLocker encryption on devices. You can do this from the Intune Administration Center. In addition, there is a Microsoft Intune Encryption Report that allows you to view details of a device's encryption status and find options for managing the device's recovery keys.
The screenshot below shows that BitLocker profile assignment was successful on almost all the devices we targeted. Note that this is the profile assignment status, not the disk encryption status.

VII - BitLocker key recovery and use
After a machine is encrypted, the encryption key will be stored on the office 365 account of the user connected to the machine (depending on the configuration we've made).
If the laptop is locked after a motherboard change, for example, you can no longer access the data on your disk. Whether Windows, Linux or any other operating system, BitLocker does not allow any attempt to access the disk unless you have your BitLocker recovery key.

At this time, as System Admin or Support Technician you can recover the BitLocker key from several locations and ways and send it to end user, I'll just mention the way with Microsoft azure :
Open the Azure AD directory (Entra ID) in the Azure portal
Go to the All users object and search for the user account associated with the device.
Click on the user object name to display the profile properties.
Go to the "Devices" object as shown in the image below.
Select the appropriate device from the list.
If the device is registered with BitLocker encryption, the BitLocker key ID and recovery key will be visible.
Click on the Copy to clipboard button and paste the data to display the complete string.


Thank you
Aymen EL JAZIRI
Microsoft MVP | Microsoft 365 Expert | Microsoft Intune Expert | Powershell Automation Expert | Microsoft 365 Security & Compliance | Microsoft Azure




Commentaires