Intune Security Deep Dive : Enable Tamper Protection to Secure Defender Settings on Windows Devices
- aymeneljaziri
- 3 juil. 2025
- 3 min de lecture

One of the most overlooked yet critical security settings on Windows endpoints is Tamper Protection. This small but powerful feature ensures that your Microsoft Defender Antivirus settings can't be modified or disabled by malware, local admins, or malicious scripts even if someone has administrative rights.
Let’s break down why it's essential and how to enforce it via Microsoft Intune in a modern environment.
1 - What is Tamper Protection ?
Tamper Protection locks down core Defender Antivirus features such as :
Real-time protection
Cloud-delivered protection
IOAV (Scan on file open)
Behavior monitoring
Automatic sample submission
Microsoft Defender Antivirus service itself
It prevents local changes, PowerShell-based bypass attempts, and unauthorized registry modifications. This is particularly important when attackers try to disable security controls before deploying malware or ransomware.
2 - Why You Should Always Enable It ?
Even with Intune-managed policies in place, a compromised local admin account could attempt to alter Defender settings using command line or registry edits. Without Tamper Protection, those changes might succeed.
With it enabled, even Set-MpPreference commands fail unless executed by Intune, MECM, or a trusted management service.
It’s a critical layer in defending against:
Ransomware attacks
Advanced persistent threats (APTs)
Post-exploitation malware activity
3 - The difference between enabling it via the Defender portal vs Intune
When enabled via Intune policy, Tamper Protection becomes a centrally managed security setting that can be deployed to specific device groups. Unlike the global toggle in the Defender portal, this method gives you granular control allowing you to assign it only to corporate-owned, Intune-enrolled Windows devices. It's ideal for organizations following Zero Trust principles, where security settings must be enforced, auditable, and compliant with broader baselines. Use this method when you want Tamper Protection to be part of your compliance strategy, integrated with Conditional Access, or combined with other Endpoint Security policies like BitLocker, ASR, and Credential Guard

4 - How to Enable Tamper Protection via Intune ✅
Tamper Protection is configured under Endpoint Security > Antivirus. Here's the step-by-step:
Go to Microsoft Intune Admin Center
Navigate to Endpoint Security > Antivirus
Click Create Policy
Under Plateform select "Windows" then "Windows Security Experience"
🔐 Important : The device must be Azure AD joined and running Windows 10 1903 or later. Co-managed devices must be configured from Intune, not MECM, to apply this setting.

Give a name and description to your policy.
Click Next

Set "Temper Protection (Device)" value to On.
Click Next

Select Group from search bar or you can just assign all devices as your company needs.
Click Next
Don't forget : Tamper Protection is per device, not per user target the right device groups.
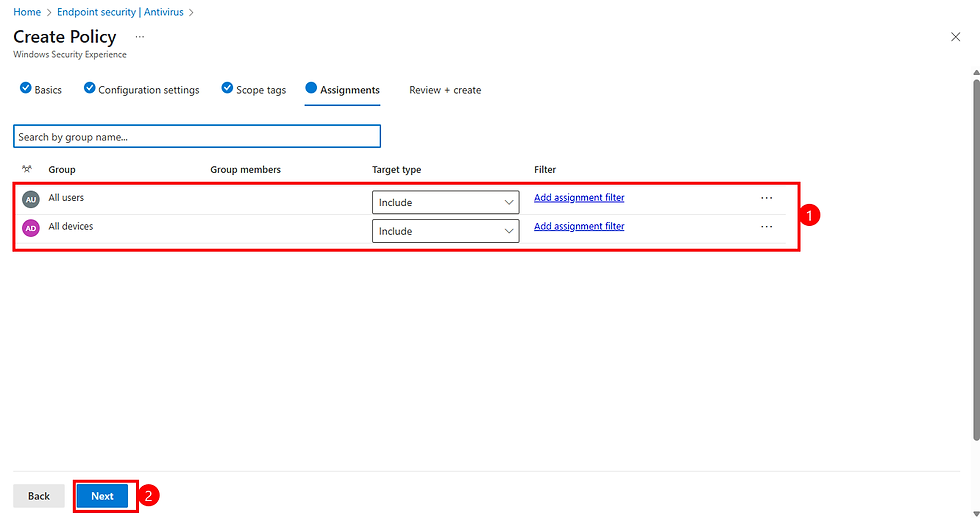
Click Save

4 - Pro Tips
5 - Final Thoughts
Tamper Protection is a must-have setting for any modern Windows security strategy. If you're relying solely on Defender but haven't enabled Tamper Protection, you're leaving a critical gap open for attackers.
In a world of increasing zero-days, lateral movement, and stealthy malware preventing tampering is not optional.
If you're managing Defender through Intune, make sure you're not just setting policies... make sure they stay enforced.
Thanks
Aymen EL JAZIRI
Lead System Administrator
Microsoft MVP




Commentaires